| Oracle Advanced Networking Option Administrator's Guide | Library |
Product |
Contents |
Index |
| Oracle Advanced Networking Option Administrator's Guide | Library |
Product |
Contents |
Index |
For more information about SQL*Net, see Understanding SQL*Net. For information on how to create the configuration files needed for Oracle networking products, see the Oracle Network Manager Administrator's Guide.
Note: Configure the Advanced Networking Option release 2.3.2 with Oracle Network Manager 3.1 or above.
See Appendix A for examples of encryption and checksumming parameters in configuration files, which you generate with Oracle Network Manager.
This guide contains generic information on how to configure your already-existing SQL*Net version 2 network to use the Advanced Networking Option. It is meant to be used in conjunction with the guide that describes how to install and configure the Advanced Networking Option on your particular platform.
Note: To use the dedicated server, configure it in the initialization file (for example, INIT.ORA). For information on how to configure the dedicated server, see the Oracle7 Server Administrator's Guide.
In a secure cryptosystem, the plaintext (a message that has not been encrypted) cannot be recovered from the ciphertext (the encrypted message) except by using the secret decryption key. In a "symmetric cryptosystem", a single key serves as both the encryption and decryption keys. DES is a secret-key, symmetric cryptosystem: when used for communication, both sender and receiver must know the same secret key, which is used both to encrypt and decrypt the message. DES is the most well-known and widely-used cryptosystem in the world. It has never been broken, despite the efforts of researchers over the last 15 years.
When encryption is used to protect the security of encrypted data, keys should be changed frequently to minimize the effects of a compromised key. For this reason, the Advanced Networking Option key management facility changes the session key with every session.
In a data modification attack, an unauthorized party on the network intercepts data in transit, and changes portions of the data before retransmitting. An example of this would be to change the dollar amount of a banking transaction. In a replay attack, an entire set of valid data is repeatedly interjected onto the network. An example would be to repeat a valid bank-account transfer transaction. The Advanced Networking Option uses a keyed, sequenced implementation of the MD5 message digest algorithm to protect against both of these forms of active attack. This protection is activated independently from the encryption features provided.
The Advanced Networking Option for Export Use contains the Diffie-Hellman key negotiation algorithm, MD5 message digest algorithm, and DES40 and RC4_40 encryption algorithms.
The Advanced Networking Option for Domestic Use contains the Diffie-Hellman key negotiation algorithm, MD5 message digest algorithm, and DES40, DES, RC4_40, RC4_56, and RC4_128 encryption algorithms.
In certain circumstances, a special license may be obtained to export the domestic version. Licenses are generally available to wholly owned subsidiaries of US corporations. Special licences can be obtained to allow banks to have the export version updated to include DES. Export and import regulations vary from country to country and change from time to time, so it is important to check on current restrictions in your area.
After the configuration files are generated and moved to appropriate machines, the SQLNET.ORA files on clients and servers using encryption and checksumming will contain some or all of the parameters listed below, depending on which ones were set in Network Manager. See Appendix A for sample SQLNET.ORA configuration files for clients or servers using the Advanced Networking Option.
| ACCEPTED | Turn on the security service if the other side wants it.
My side of the connection does not desire the security service, but it will be allowed if the other side asks with a setting of REQUIRED or REQUESTED. If the other side is set to REQUIRED or REQUESTED and an algorithm match is found, the connection will continue without error and with the security service turned on. If the other side is set to REQUIRED and no algorithm match is found, the connection will terminate with error message 12650. If the other side is set to REQUESTED and no algorithm match is found, or if the other side is set to ACCEPTED or REJECTED, the connection will continue without error and without the security service enabled. The default value is ACCEPTED. If you do not specify a value for a parameter, it defaults to ACCEPTED. |
| REJECTED | Do not turn on the security service even if the other side wants it. My side of the connection specifies that the security service is not allowed. If the other side specifies REQUIRED, the connection will terminate with error message 12650. If the other side is set to REQUESTED, ACCEPTED, or REJECTED, the connection will continue without error and without the security service enabled. |
| REQUESTED | Turn on the security service if the other side allows it. My side of the connection specifies that the security service is desired, but not required. The security service will be active if the other side specifies ACCEPTED, REQUESTED, or REQUIRED. There must be a matching algorithm available on the other side; otherwise, the service will not be activated. If the other side specifies REQUIRED and there is no matching algorithm, the connection fails. |
| REQUIRED | Turn on the security service or do not make the connection. My side of the connection specifies that the security service must be activated. The connection will fail if the other side specifies REJECTED, or if there is no compatible algorithm on the other side. |
| Client | |||||
| Accepted | Rejected | Requested | Required | ||
| Accepted | OFF | OFF | ON | ON | |
| Server | Rejected | OFF | OFF | OFF | connection will fail |
| Requested | ON | OFF | ON | ON | |
| Required | ON | connection will fail | ON | ON | |
Also, you configure these parameters for clients and servers by generating a Client Profile for each set of clients and servers with a particular set of properties. Refer to the Oracle Network Manager Administrator's Guide for more information.
Refer to "Negotiating Encryption and Checksumming" ![[*]](jump.gif) for descriptions of possible values you can specify for four of the parameters.
for descriptions of possible values you can specify for four of the parameters.
This parameter specifies the desired behavior when a client (or a server acting as a client) is connecting to this server. The behavior of the server will depend in part on the SQLNET.ENCRYPTION_CLIENT setting at the other end.
Possible values: ACCEPTED, REJECTED, REQUESTED, REQUIRED
Default value: ACCEPTED
Note: If no value is specified in Network Manager, the Advanced Networking Option defaults this parameter to ACCEPTED (even if this parameter does not exist in the SQLNET.ORA file).
Possible values: ACCEPTED, REJECTED, REQUESTED, REQUIRED
Default value: ACCEPTED
Note: If no value is specified in Network Manager, the Advanced Networking Option defaults this parameter to ACCEPTED (even if this parameter does not exist in the SQLNET.ORA file).
where valid_encryption_algorithm is one of:
RC4_40 RSA RC4 (40-bit key size)
Domestic & International
RC4_56 RSA RC4 (56-bit key size)
Domestic only
RC4_128 RSA RC4 (128-bit key size) Domestic only
DES Standard DES (56-bit key size)
Domestic only
DES40 DES40 (40-bit key size)
Domestic & International
This parameter specifies a list of encryption algorithms this server is allowed to use when acting as a server. This list is used to negotiate a mutually acceptable algorithm with the other end of the connection. Specify algorithms in the order of desired use, with the most desired algorithm listed first. Each algorithm will be checked against the list of client algorithm types available until a match is found. If an algorithm that is not installed is specified on this side, the connection will terminate with error message 12650.
Default value: All installed algorithms will be used if no algorithms are selected on Server Encryption page.
Domestic version: If you are using the Domestic version, all four algorithms are installed: RC4_40, RC4_56, RC4_128, DES, and DES40. If no algorithms are selected on the Server Encryption page, the installed algorithms will be used in the following order to negotiate a mutually acceptable algorithm with the other end of the connection: RC4_40, RC4_56, RC4_128, DES, and DES40.
Export version: If you are using the Export version, the following algorithms are installed: RC4_40 and DES40. If no algorithms are selected on the Client Encryption page, the installed algorithms will be used in the following order to negotiate a mutually acceptable algorithm: RC4_40 and DES40.
To change the order of algorithms on the Server Encryption page, use the Demote button.
You can specify multiple encryption algorithms, that is, either a single value or a list of algorithm names. For example, either of the following encryption parameters is acceptable:
SQLNET.ENCRYPTION_TYPES_SERVER=(DES,RC4_56,RC4_128, DES40
SQLNET.ENCRYPTION_TYPES_SERVER=(RC4_40)
where valid_encryption_algorithm is one of:
RC4_40 RSA RC4 (40-bit key size)
Domestic & International
RC4_56 RSA RC4 (56-bit key size)
Domestic only
DES Standard DES (56-bit key size)
Domestic only
DES40 DES40 (40-bit key size)
Domestic & International
This parameter specifies a list of encryption algorithms this client (or this server acting as a client) is allowed to use when connecting to a server. This list is used to negotiate a mutually acceptable algorithm with the other end of the connection. The parameters can be listed in any order. If an algorithm that is not installed is specified on this side, the connection will terminate with error message 12650.
Default value: All installed algorithms will be used (if no algorithms are selected on Client Encryption page).
Domestic version: If you are using the Domestic version, all four algorithms are installed: RC4_40, RC4_56, DES, and DES40. If no algorithms are selected on the Client Encryption page, the installed algorithms will be used in the following order to negotiate a mutually acceptable algorithm with the other end of the connection: RC4_40, RC4_56, DES, and DES40.
Export version: If you are using the Export version, the following algorithms are installed: RC4_40 and DES40. If no algorithms are selected on the Server Encryption page, the installed algorithms will be used in the following order to negotiate a mutually acceptable algorithm: RC4_40 and DES40.
To change the order of algorithms on the Client Encryption page, use the Demote button.
You can specify multiple encryption algorithms, that is, either a single value or a list of algorithm names. For example, either of the following encryption parameters is acceptable:
SQLNET.ENCRYPTION_TYPES_CLIENT=(DES, DES40, RC4_56, RC4_40)
SQLNET.ENCRYPTION_TYPES_CLIENT=(RC4_40)
This parameter specifies the desired checksum behavior when a client (or another server acting as a client) is connecting to this server. The resulting behavior will depend in part on the SQLNET.CRYPTO_CHECKSUM_CLIENT setting at the other end.
Possible values: ACCEPTED, REJECTED, REQUESTED, REQUIRED
Default value: ACCEPTED
Note: If no value is specified in Network Manager, the Advanced Networking Option defaults this parameter to ACCEPTED (even if this parameter does not exist in the SQLNET.ORA file).
This parameter specifies the desired checksum behavior when this client (or this server acting as a client) is connecting to a server. The resulting behavior will depend in part on the SQLNET.CRYPTO_CHECKSUM_SERVER setting at the other end of the connection.
Possible values: ACCEPTED, REJECTED, REQUESTED, REQUIRED
Default value: ACCEPTED
Note: If no value is specified in Network Manager, the Advanced Networking Option defaults this parameter to ACCEPTED (even if this parameter does not exist in the SQLNET.ORA file).
where crypto_checksum_algorithm is:
MD5
Currently, the only supported crypto-checksum algorithm choice is RSA Data Security's MD5 algorithm. Other algorithms may be supported in future releases.
This parameter specifies a list of the checksumming algorithms this server is allowed to use when acting as a server to a client or another server. This list is used to negotiate a mutually acceptable algorithm with the remote end. Specify algorithms in order of desired use, with the most desired algorithm listed first. Each algorithm will be checked against the list of client algorithm types available until a match is found, which will then be used. If an algorithm is specified that is not installed on this side, the connection will terminate with error message 12650.
Default value: MD5 (currently the only valid value)
This parameter specifies a list of checksumming algorithms this client (or this server acting as a client) is allowed to use when connecting to a server. This list is used to negotiate a mutually acceptable algorithm with the remote end. The order in which the algorithms are listed is not important. If an algorithm that is not installed on this side is specified, the connection will terminate with error message 12650.
Default value: MD5 (currently the only valid value)
The characters in the Encryption field are used when generating cryptographic keys. The more random the characters entered into this field are, the stronger the keys are. You set this parameter by entering from ten to 70 characters into the Encryption field on the Client Profile General Page in Network Manager, or you can use the default value provided by Network Manager.
Note: It is recommended that you enter as many characters as possible (up to 70) since the resulting key will be more random and therefore stronger.
Note: This parameter must be present in the SQLNET.ORA file whenever encryption or checksumming is turned on.
Note: Sample configuration files for encryption and checksumming are shown in Appendix A. For information on configuring authentication, refer to Chapters 3, 4, and 5 and Appendix C.
Edit the Client Profile for all servers and clients to configure a set of clients and servers with similar characteristics. Refer to Figure 2 - 1 through Figure 2 - 5.
 Figure 2 - 1. Editing Client Profile to Set the Encryption Seed
Figure 2 - 1. Editing Client Profile to Set the Encryption Seed
Attention: For added security, Oracle recommends that you enter your own value for the encryption seed--do not use the default. Network Manager will generate a new encryption seed every time new configuration files are generated.
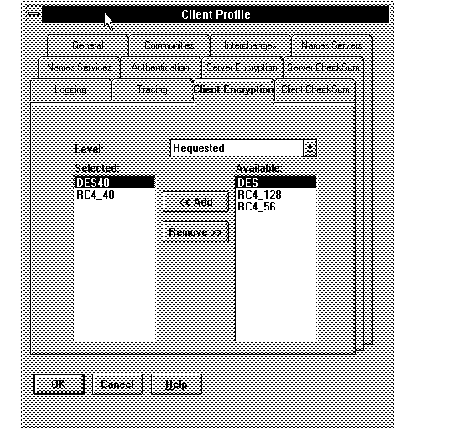 Figure 2 - 2. Editing Client Profile to Set Up Encryption for a Set of Clients
Figure 2 - 2. Editing Client Profile to Set Up Encryption for a Set of Clients
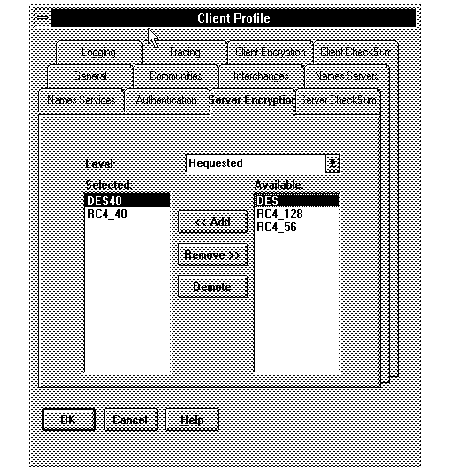 Figure 2 - 3. Editing Client Profile to Configure Encryption for a Set of Servers
Figure 2 - 3. Editing Client Profile to Configure Encryption for a Set of Servers
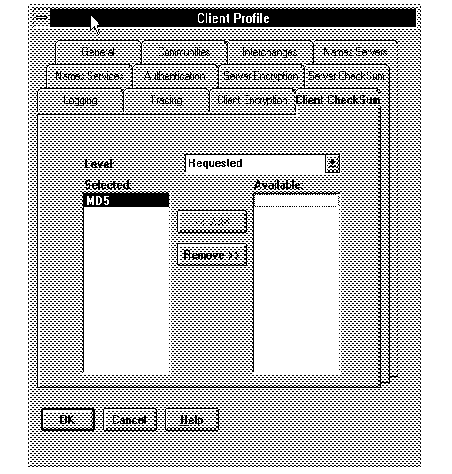 Figure 2 - 4. Editing Client Profile to Configure Checksumming for a Set of Clients
Figure 2 - 4. Editing Client Profile to Configure Checksumming for a Set of Clients
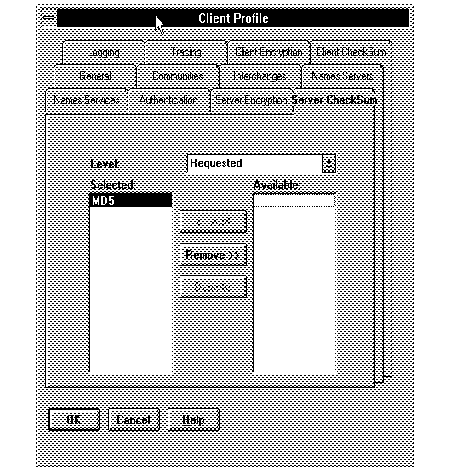 Figure 2 - 5. Editing Client Profile to Configure Checksumming for a Set of Servers
Figure 2 - 5. Editing Client Profile to Configure Checksumming for a Set of Servers
You have just configured all servers and clients in the current client profile to use encryption and checksumming. Similarly, you have just configured all servers in the current client profile to act as encryption and checksumming servers.
Note: For a sample of how the SQLNET.ORA file would look after performing the previous actions, see "Sample SQLNET.ORA Configuration Files for Clients and Servers" in Appendix A.
|
Prev Next |
Copyright © 1996 Oracle Corporation. All Rights Reserved. |
Library |
Product |
Contents |
Index |