| Understanding SQL*Net | Library |
Product |
Contents |
Index |
| Understanding SQL*Net | Library |
Product |
Contents |
Index |
Configure the network using the Oracle Network Manager. Once the configuration files are on the destination machines, each component can be started and tested. The preferred sequence for testing the network is to:
NAMESCTL> STARTUP
To test that a Names Server is operating correctly, use the PING command. Following are two ways to PING the server LABRADOR in the US.ACME domain. Alternatively, you can use TNSPING (described on page 5-5).
NAMESCTL> PING LABRADOR.US.ACME
or
NAMESCTL> SET SERVER LABRADOR.US.ACME
NAMESCTL> PING
You can also PING multiple Names Servers by using a single command, for example:
NAMESCTL>PING HUEY.UK.ACME DUEY.UK.ACME LOUIE.UK.ACME
PING responds with the time it takes to contact the Names Server and return an acknowledgment.
If PING fails, make sure the Names Server has been started. If it has been, double-check the configuration in Network Manager, especially the defined address of the Names Server in question.
LSNRCTL START
To start a non-default listener:
LSNRCTL START listener_name
LSNRCTL will display a status message indicating that it has started successfully. After LSNRCTL has started the listener, it has no further control over the listener. Check that all expected SIDs for that listener are listed in the services summary in the status message. For more information on the Listener Control Utility see the section "Using the Listener Control Utility" later in this chapter.
The simplest test uses SQL*Plus as follows:
SQLPLUS user/password@service_name
The service_name may be found in the TNSNAMES.ORA file, an Oracle Names Server, or a native naming service such as NIS or DCE's CDS. For more information on testing SQL*Net from a client, see the section "Initiating a SQL*Net Connection" later in this chapter.
If there are no clients in the same community as the listener, you must start an Interchange before testing the listener.
Repeat these steps for each listener in the network.
INTCTL START INTERCHANGE
or
INTCTL START INT
INTCTL displays a status message indicating that it has started successfully. For more information on the Interchange Control Utility see Chapter 6, "Controlling the MultiProtocol Interchange," in the Oracle MultiProtocol Interchange Administrator's Guide.
SQLPLUS user/password@service_name
The service_name for the database in the other community may be stored in TNSNAMES.ORA, an Oracle Names Server, or a native naming service such as NIS or DCE's CDS. To ensure that the connection went through the Interchange, type:
INTCTL STATUS INTERCHANGE
The Connection Manager should indicate that there is one active connection through the Interchange. You can run the STATUS command on the Interchange machine. If the Interchange is listed in the TNSNAMES.ORA file, stored in an Oracle Names Server, or stored in a native naming service, then you can run the STATUS command remotely from any other node.
NAMESCTL> QUERY global_object_name type
Database service names have the type A.SMD, and database links have the type DL.RDBMS.OMD. The following example shows a query of the database service name BUGSY in the MACS.ACME domain.
NAMESCTL> QUERY BUGSY.MACS.ACME A.SMD
The QUERY command returns the amount of time the transaction took and information about the network object.
If you can connect successfully to a TNS service using TNSPING, it displays an estimate of the round trip time (in milliseconds) it takes to reach the Oracle service. If it fails, it displays a message describing the error that occurred. This allows you to see the network error that is occurring without the overhead of a database connection.
You invoke TNSPING on the command line as follows:
tnsping service_name count
On some platforms, such as Microsoft Windows, the interface may be different, but the program accepts the same arguments.
tnsping spotdb
produces the following message:
TNS Ping Utility for SunOS: Version 2.2.2.0.0 - Production on 10-Mar-95 10:09:13
Copyright (c) Oracle Corporation 1995. All rights reserved.
Attempting to contact (ADDRESS=(COMMUNITY=build_tcp.us.oracle.com)(PROTOCOL=TCP) (HOST=spot)(PORT=1599)) OK (50msec)
To check whether an Oracle Names Server can be reached, use a command similar to the following:
tnsping (ADDRESS=(COMMUNITY=build_tcp.us.oracle.com) (PROTOCOL=TCP)(HOST=fido)(PORT=1600))
The address of the Oracle Names Server is located in SQLNET.ORA (in the NAMES.PREFERRED_SERVERS and NAME.PREFERRED_SERVERS parameters) on the client.
Note: Both parameters showing the client's preferred Names Server must be included for backward compatibility with an earlier version of the product.
A message similar to the following will be returned to the user:
TNS Ping Utility for SunOS: Version 2.2.2.0.0 - Production on 10-Mar-95 10:09:59
Copyright (c) Oracle Corporation 1995. All rights reserved.
Attempting to contact (ADDRESS=(COMMUNITY=build_tcp.us.oracle.com) (PROTOCOL=TCP)(HOST=fido)(PORT=1600))
OK (70 msec)
To determine whether the STPRD database can be connected to, and to specify that TNSPING try to connect 10 times and then give up, use the following command:
tnsping stprd 10
This command produces the following message:
TNS Ping Utility for SunOS: Version 2.2.2.0.0 - Production on 10-Mar-95 10:10:28
Copyright (c) Oracle Corporation 1995. All rights reserved.
Attempting to contact (ADDRESS=(COMMUNITY=build_tcp.us.oracle.com) (PROTOCOL=TCP)(HOST=spot)(PORT=1599))
OK (290 msec)
OK (100 msec)
OK (70 msec)
OK (70 msec)
OK (60 msec)
OK (70 msec)
OK (70 msec)
OK (80 msec)
OK (180 msec)
OK (340 msec)
Below is an example of TNSPING attempting to connect to an invalid service name:
tnsping invalid_service_name
This attempt produces the following message:
TNS Ping Utility for SunOS: Version 2.2.2.0.0 - Production on 10-Mar-95 10:10:58
Copyright (c) Oracle Corporation 1995. All rights reserved.
TNS-03505: Failed to resolve name
Following is an example of using TNSPING to connect to a name that is valid, but that resolves to an address where no server is located (for example, the server may be down or not started):
tnsping testing
The following message is returned:
TNS Ping Utility for SunOS: Version 2.2.2.0.0 - Production on 10-Mar-95 10:11:42
Copyright (c) Oracle Corporation 1995. All rights reserved.
Attempting to contact (ADDRESS=(PROTOCOL=tcp)(HOST=spot)(PORT=1599)) TNS-12541: TNS:no listener
LSNRCTL command [listener_name]
In this syntax:
LSNRCTL
command
Specifies the action to be performed.
listener_name
Specifies the listener name defined in LISTENER.ORA. If listener_name is not included, the default value LISTENER is used.
You can also issue Listener Control commands at the program prompt. When you enter LSNRCTL on the command line, the program is opened. You can then enter the desired commands from the program prompt. For example, the following command starts the database subagent for a node managed by SNMP support.
LSNRCTL> dbsnmp_start
iris[331] lsnrctl LSNRCTL for SunOS: Version 2.3.1.1.0 - Beta on 17-AUG-95 17:15:02 Copyright (c) Oracle Corporation 1994. All rights reserved. Welcome to LSNRCTL, type "help" for information.
LSNRCTL> help The following operations are available An asterisk (*) denotes a modifier or extended command: start stop status services version reload trace spawn dbsnmp_start dbsnmp_stop dbsnmp_status change_password quit exit set* show*
LSNRCTL> set The following operations are available after set An asterisk (*) denotes a modifier or extended command: password trc_file trc_directory trc_level log_file log_directory log_status current_listener connect_timeout startup_waittime use_plugandplay
LSNRCTL> show The following operations are available after show An asterisk (*) denotes a modifier or extended command: trc_file trc_directory trc_level log_file log_directory log_status current_listener connect_timeout startup_waittime snmp_visible use_ckpfile use_plugandplay
change_password
The control utility prompts you for your old password, then for the new one. It asks you to re-enter the new one, then changes it.
Note: Neither the old nor the new password displays during this procedure.
The following is an example of changing a password:
iris> lsnrctl LSNRCTL for SunOS: Version 2.3.2.0.0 - on 10-Sep-95 18:59:34 Copyright (c) Oracle Corporation 1994. All rights reserved. Welcome to LSNRCTL, type "help" for information. LSNRCTL> change_password Old password: New password: Reenter new password: Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) Password changed for LISTENER The command completed successfully LSNRCTL>
For example, you might create a program called NSTEST, and manually add the following to the LISTENER.ORA file:
nstest = (PROGRAM=(NAME=nstest)(ARGS=test1)(ENVS='ORACLE_HOME=/usr/oracle'))
To run the NSTEST program, you would enter the following:
lsnrctl spawn nstest
Note: You must have set a valid password if one is listed in the LISTENER.ORA parameter PASSWORDS_listener_name to be able to use this command.
Note: You must have set a valid password if one is listed in the LISTENER.ORA paramete,r PASSWORDS_listener_name, to be able to use this command.
Note: You must have set a valid password, if one is listed in the LISTENER.ORA file parameter PASSWORDS_listener_name, to be able to use this command.
Note: You must have set a valid password, if one is listed in the LISTENER.ORA file parameter PASSWORDS_listener_name, to be able to use this command.
For detailed information on how to use tracing, see the Oracle Network Products Troubleshooting Guide.
DBSNMP START must be run locally--you cannot run it remotely.
DBSNMP STOP must be run locally--you cannot run it remotely.
DBSNMP STATUS must be run on the same node the Oracle database is on.
The preferred, secure way to enter your password is in interactive mode. Enter the command from within LSNRCTL, for example,
LSNRCTL> SET PASSWORD
The Listener Control Utility responds:
enter listener password:
When you enter your password and press [Return], the password is not echoed on the terminal. You receive the message:
Command successful
Note: You must enter the SET PASSWORD command before you can stop the listener (with the STOP [listener_name)
Note: The listener supports encrypted and unencrypted passwords.
Note: You must have set a valid password, if one is listed in the LISTENER.ORA file parameter PASSWORDS_listener_name to be able to use this command.
For detailed information on how to use tracing, see the Oracle Network Products Troubleshooting Guide.
For example, the following command sets the name of the file that contains listener trace information:
LSNRCTL> set trc_file list.trc
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "trc_file" set to list.trc The command completed successfully
For example, the following command sets the directory in which the trace file is placed:
LSNRCTL> set trc_directory /usr/oracle/admin
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "trc_directory" set to /usr/oracle/admin The command completed successfully
For example, the following command sets the name of the file that contains listener log information:
LSNRCTL> set log_file list.trc
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "log_file" set to list.log The command completed successfully
For example, the following command sets the directory in which the log file is placed:
LSNRCTL> set log_directory /usr/oracle/admin
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "log_directory" set to /usr/oracle/admin The command completed successfully
For example, suppose there were two listeners on a node, LISTENER and LSNR1. If you wanted to set or show parameters for LSNR1, you would first need to send the following command from within LSNRCTL:
LSNRCTL> set current_listener lsnr1
Any subsequent LSNRCTL commands within the same LSNRCTL session would then apply to LSNR1, unless CURRENT_LISTENER were reset. For example, if the current listener had been set to LSNR1, then the STAT command would produce something like the following output:
LSNRCTL> stat
Connecting to (ADDRESS=(PROTOCOL=IPC)(KEY=IRIS)) STATUS of the LISTENER ----------------------- Alias lsnr1 Version TNSLSNR for SunOS: Version 2.3.1.1.0- Beta Start Date 18-Aug-95 11:25:45 Uptime 0 days 0 hr. 0 min. 3 sec Trace Level admin Security OFF SNMP ON Listener Parameter File /etc/oracle/network/admin/listener.ora Listenr Log File /etc/oracle/network/log/lsnr1.log Listener Trace File /etc/oracle/network/trace/lsnr1.trc Services Summary... db1 has 1 service handler(s) The command completed successfully
You can also display the current listener by using the LSNRCTL SHOW command.
Note: You must enter SET CURRENT_LISTENER from within the LSNRCTL utility. When you exit the utility, the setting will be lost.
LSNRCTL> set connect_timeout 20
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "connect_timeout" set to 20 The command completed successfully
lSNRCTL> set startup_waittime 10
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "startup_waittime" set to 10 The command completed successfully
LSNRCTL> set use_plugandplay ON|OFF
By default, the value of this parameter is OFF. If Oracle Names version 2 has been installed, and you want the listener to use the Dynamic Discovery Option (that is, to register itself with a well-known Names Server, set it to ON. You can also set the value in LISTENER.ORA through Oracle Network Manager, which places a slightly different parameter into LISTENER.ORA, as follows:
use_plugandplay_listener_name=[ON|OFF]
If the Dynamic Discovery Option is enabled, you can use the LSNRCTL STATUS command to see whether a service has registered itself. For example:
LSNRCTL> stat lsnr1
Connecting to (ADDRESS=(PROTOCOL=IPC)(KEY=IRIS)) STATUS of the LISTENER ----------------------- Alias lsnr1 Version TNSLSNR for SunOS: Version 2.3.1.1.0- Beta Start Date 18-Aug-95 11:25:45 Uptime 0 days 0 hr. 1 min. 49 sec Trace Level admin Security OFF SNMP ON Listener Parameter File /etc/oracle/network/admin/listener.ora Listener Log File /etc/oracle/network/log/lsnr1.log Listener Trace File /etc/oracle/network/trace/lsnr1.trc Services Summary... db1 (Registered) has 1 service handler(s) The command completed successfully
In addition, there are two other parameters that can be shown, but not set, through LSNRCTL.
LSNRCTL> show snmp_visible
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "snmp_visible" set to ON The command completed successfully
Note: The SNMP_VISIBLE parameter can be displayed, but not set, through LSNRCTL:
LSNRCTL> show use_ckpfile
The computer output would be something like the following:
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=iris)) LISTENER parameter "use_ckpfile" set to OFF The command completed successfully
If USE_CKPFILE_listener_name is not set in LISTENER.ORA, and you use LSNRCTL SET commands to change listener parameters, when you stop the listener, LSNRCTL sends a message reminding you that the changes you have made are not persistent.
Note: You cannot set this parameter using LSNRCTL; it must be set in LISTENER.ORA. For more information about the use of checkpoint files, see "Persistent Changes" later in this chapter.
use_ckpfile_listener_name=ON
If this parameter is in the LISTENER.ORA file, the parameters you set using LSNRCTL are saved to a checkpoint file, listener_name.CKP, either in the TNS_ADMIN directory if one exists, or in the ORACLE_HOME/NETWORK/ADMIN directory. The values in this checkpoint file will override the values set in LISTENER.ORA.
If the USE_CKPFILE parameter is set to OFF in LISTENER.ORA, the values set by LSNRCTL are lost when the listener is restarted or the LISTENER.ORA parameters are reloaded. The default is for USE_CKPFILE to be OFF.
Note: If checkpointing is enabled and parameters in LISTENER.ORA are changed, the changes will not be visible because they are overridden by the parameters in the checkpoint file. If you want the changes in LISTENER.ORA to be visible, set the value of USE_CKPFILE to OFF and use the LSNRCTL RELOAD command to reread the LISTENER.ORA file.
LSNRCTL START
Alternatively, you can enter LSNRCTL on the command line and then enter START from the program prompt.
To start a listener configured in the LISTENER.ORA file with a name other than LISTENER, include that name. For example, if the listener name is TCP_LSNR, enter:
LSNRCTL START TCP_LSNR
Or, from the LSNRCTL program prompt, just enter:
LSNRCTL> START TCP_LSNR
LSNRCTL STOP
To stop a running listener defined in LISTENER .ORA as TCP_LSNR, use the command:
LSNRCTL STOP TCP_LSNR
Remember, if there are any passwords in the LISTENER.ORA file, you must use the SET PASSWORD command before you can use the STOP command. You must set the password from within the LSNRCTL program; you cannot set it from the operating system command line. The method for setting the password depends on whether you are using the encrypted password feature. If you are not using an encrypted password, enter the password on the LSNRCTL command line. For example, the following commands stop the TCP_LSNR using an unencrypted password:
LSNRCTL LSNRCTL> SET PASSWORD password LSNRCTL> STOP TCP_LSNR
If you are using an encrypted password, enter the password in interactive mode. For example, the following commands stop the listener named TCP_LSNR:
LSNRCTL LSNRCTL> SET PASSWORD
Enter listener password (password is not displayed) Command successful LSNRCTL> STOP TCP_LSNR
Stopping a listener when in batch mode is not recommended, because to do so you must include your password in a cleartext batch file, which would threaten your security. However, if you are not using an encrypted password, stopping a listener can be done by redirecting input into the command interpreter.
Note: You should not stop the listener in batch mode if it requires an encrypted password.
Different operating systems use different syntax. An example for VMS and two alternative methods for UNIX follow.
To stop a listener in batch mode on VMS, create a DCL script, with a name like LSNRSTOP.COM, as follows:
$ lsnrctl set password password stop listener_name exit
When you want to stop the listener, run the script as follows:
@LSNRSTOP
On a UNIX system or on OS/2, the following procedure would be effective:
Create a file with a name like LSNRSTOP that contains the following lines:
set password password stop listener_name
You can then stop the listener from the command line by entering:
lsnrctl < LSNRSTOP
Alternatively, in UNIX you can stop the listener by creating a shell script named something like "lsnrstop". The shell script would look something like this::
lsnrctl <<! set password password stop listener_name exit !
You can then stop the listener from the command line by entering:
LSNRSTOP
Again, Oracle Corporation recommends against stopping a listener in batch mode because of the need to expose your password.
Note: Be careful when stopping a listener. On some platforms and with some protocols, when a listener is stopped any SQL*Net connections currently running are shut down. In some situations the connections continue, but it is then not possible to start the listener again until the running processes have been closed. It is good practice to send a warning message to all network users before stopping a listener.
LSNRCTL STATUS
Following is sample output from a status report of a UNIX listener :
LSNRCTL for SunOS: Version 2.2.2.0 - Production on 15-FEB-95 07:07:10
Copyright (c) Oracle Corporation 1995. All rights reserved.
Connecting to (ADDRESS=(PROTOCOL=IPC)(HOST=orchid)(port=1334))
STATUS of the LISTENER
------------------------
Alias LISTENER
Version TNSLSNR for SunOS: Version 2.2.2.0 -
Production
Start Date 10-FEB-94 07:06:34
Uptime 0 days 0 hr. 0 min. 44 sec
Trace Level ADMIN
Security ON
SNMP ON
Listener Parameter File /private1/dvl/7012/network/admin/listener.ora
Listener Log File /private1/dvl/7012/network/log/listener.log
Listener Trace File /private1/dvl/7012/network/trace/listener.trc
Listening on (ADDRESS=(PROTOCOL=tcp)(HOST=orchid)
(port=1334)))
(ADDRESS=(PROTOCOL=decnet)(node=23.106)
(object=orchid)))
Services Summary...
orchid has 1 service handlers
The command completed successfully
LSNRCTL>[SET PASSWORD password] LSNRCTL> SERVICES
The output of a LSNRCTL SERVICES command follows:
LSNRCTL for SunOS: Version 2.1.3.0.0 - Production on 10-FEB-94 07:14:55
Copyright (c) Oracle Corporation 1993. All rights reserved.
Connecting to (ADDRESS=(PROTOCOL=IPC)(KEY=ruth))
Services Summary...
ruth has 1 service handlers
DEDICATED SERVER established:99 refused:0
The LSNRCTL command completed successfullyIn this example, the LSNRCTL SERVICES command returned the information that the listener had established 99 connections using a dedicated server process and refused none.
In the following example the LSNRCTL SERVICES command returns information about four types of service handlers.
LSNRCTL for SunOS: Version 2.2.2.0.0 - Production on 15-Mar-1995 17:41:12
Copyright (c) Oracle Corporation 1994. All rights reserved.
Connecting to (ADDRESS=(PROTOCOL=ipc)(KEY=orchid))
Services Summary...
listener has 4 service handlers
DEDICATED SERVER established:0 refused:0
PRESPAWNED SERVER established:0 refused:0 current:0 max:1 state:ready
PID:15439
(ADDRESS=(PROTOCOL=ipc)(DEV=4)(KEY=#15439.1))
PRESPAWNED SERVER established:5 refused:0 current:0 max:1 state:ready
PID:15441
(ADDRESS=(PROTOCOL=tcp)(DEV=4)(HOST=139.185.22.25)(PORT=3334))
DISPATCHER established:30 refused:0 current:7 max:21 state:ready
D000 (machine: orchid, pid: 15406)
(ADDRESS=(PROTOCOL=tcp)(DEV=7)(HOST=139.185.22.25)(PORT=3330))
The command completed successfully
This message shows that since this listener has been running, it has made a total of five connections using a prespawned server for TCP/IP, and that it has one running at this time. It also shows that there are seven connections currently established using a multi-threaded server dispatcher, with a total of 30 established since the process started.
Alternatively, if you want to change parameters for individual clients, you may use the SQLNET.ORA Editor. This utility is part of the Client Status Monitor. It enables you to open the SQLNET.ORA file on an individual client and change its parameters either through a graphical user interface or through the command line.
If you are using Oracle Names version 2.0 and the Dynamic Discovery Option, you do not necessarily need to use Network Manager. If you do not use it, a SQLNET.ORA file is not created. If you find you want to provide some non-default parameters for the client, you can create an empty SQLNET.ORA using any text editor, such as vi, and then add the parameters you need using the SQLNET.ORA Editor. Using this method to create the file makes it less likely that typographical or formatting mistakes will cause errors.
After your network has been defined, you can obtain information on any network service by selecting it on the Map View or Tree View Object List and then selecting Control Network Service from the Special menu.
Note: You must define the network configuration and distribute the configuration files throughout the network before you can use this option.
A control window appears. Select a command from the drop-down list. (The commands available depend on the type of network object you have selected.) For example, if you select Trace, select the level of tracing you want from the Level list. The result of your command will be displayed in the large read-only box on this window.
Following are the commands you can use from Network Manager to control network services remotely.
LSNRCTL
VERSION STATUS RELOAD SET_TRACE_LEVEL SERVICES
NAMESCTL
VERSION STATUS PING SET TRACE_LEVEL SHOW TRACE_LEVEL
INTCTL
VERSION STATUS
The Listener Control Utility (LSNRCTL) commands are described in "Using the Listener Control Utility" in this chapter. See the Oracle Names Administrator's Guide for information on NAMESCTL commands. See the Oracle MultiProtocol Interchange Administrator's Guide for information on INTCTL commands.
tool username/password@service_name
In this syntax:
tool
Specifies the command used to invoke a tool such as SQL*Plus, SQL*Forms, etc.
username
Specifies an Oracle username on the server.
password
Specifies the corresponding password on the server.
service_name
Specifies a service name entered in the TNSNAMES.ORA file that identifies the connect descriptor for the desired server. If the server is in the client's default domain, the service name does not need to include the domain name. However, if the server is in another domain, the service name must include the domain. (The default domain is determined by a parameter in the client's SQLNET.ORA file. See the section on the SQLNET.ORA file in Appendix A of this manual.)
For example, in a network with only one domain, the default .WORLD domain, it is not necessary to include .WORLD in the service name. For example:
% sqlplus scott/tiger@SERVERX
However, if the client's default domain were .EAST and the server's domain were .WEST, then the service name would have to include the domain. For example,
% sqlplus scott/tiger@SERVERX.WEST
Most Oracle tools can use the operating system command line to connect; some provide alternatives.
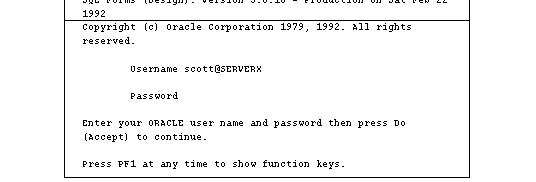
Figure 5 - 1. Connection from Logon Screen
EXEC SQL CONNECT :username IDENTIFIED BY :password
In this connection request, the :username and :password are 3GL variables that can be set within the program either statically or by prompting the user. When connecting to a database server, the value of the :username variable is in the form:
username@service_name
which is the same as in the tool logon screen above. The :password variable contains the password for the database account being connected to.
SQL> CONNECT username/password@service_name
For example:
SQL> CONNECT SCOTT/TIGER@SERVERX
This is very similar to the operating system command line method, except that it is entered in response to the tool prompt instead of the operating system prompt.
Other Oracle tools use slightly different methods specific to their function or interface. For example, Oracle CDE tools use logon buttons and a pop-up window with the username, password, and remote database ID field. For more information on connecting to Oracle with a specific tool, refer to the tool's user guide.
Listener load balancing is also useful in a multiple server environment, in which there can be multiple listeners that listen for replicated servers.
For more detailed information about listener load balancing, see "Listener Load Balancing" in Chapter 2. For information about configuring multiple listeners, see "Configuring Listener Load Balancing," in Appendix A.
This feature is appropriate in a heavily loaded system when connect times are slow and Multi-threaded Servers are not used.
Note: Async and APPC/LU6.2 protocols do not support this feature.
For more information about prestarted processes, see "How SQL*Net Establishes Connection to a Prestarted Dedicated Server," in Chapter 2.
The default SDU size is 2048. It is adjustable from 512 to 32K.
SDU size should be set on both the client and server sides, and should generally be the same; if different SDU sizes are requested on the client and the server, the SDU size is negotiated down to the lower of the two.
(SDU=number)
Be sure to include the parentheses. The parameter and value appear in both the LISTENER.ORA file and the TNSNAMES.ORA file.
An example of how it might appear in the LISTENER.ORA file follows:
... (SID_DESC= (SDU=4096) (SID_NAME=dbprod))
An example of how it might appear in the TNSNAMES.ORA file follows:
DESCRIPTION= (SDU=4096) (ADDRESS_LIST= ...
Note: A user can change the client side request for SDU size by manually editing TNSNAMES.ORA, but the SDU size used will be the lower of the SDU size listed in LISTENER.ORA and TNSNAMES.ORA. Therefore, if SDU size is not listed in the LISTENER.ORA file, the SDU size used will not be greater than the default of 2048.
Note: If your network uses Oracle Names, a global database link is created on every database on the network to every other database. Therefore, you do not need to create additional database links, as described in this section. See "Database Links wth Oracle Names" later in this chapter.
The generic syntax for creating a database link in SQL is:
CREATE [PUBLIC] DATABASE LINK linkname [CONNECT TO username IDENTIFIED BY password] USING 'service_name'
In this syntax:
[PUBLIC]
Specifies a database link available to all users with the CREATE SESSION privilege. If the PUBLIC option is omitted, a private link available only to the creator is created. Note that creating a public database link requires CREATE PUBLIC DATABASE LINK privilege.
linkname
Specifies the name of the database link. If the remote server is in the local server's domain, the link name does not need to include the domain name. However, if the server is in another domain, the link name must include the domain. (The domain is determined by DB_DOMAIN in the initialization parameter file).
CONNECT TO
Optionally specifies a single username and password for all users of the database link to share. If the clause is omitted, the Oracle username and password of the user account using the database link will be used to connect to the remote database server.
username
Specifies a valid Oracle username on the remote database server.
password
Specifies the corresponding password of the username on the remote database server.
service_name
Specifies the service name defined in the TNSNAMES.ORA file or stored in Oracle Names associated with the connect descriptor for the desired database. If the remote server is in the local server's default domain, the service name does not need to include the domain name. However, if the server is in another domain, the service name must include the domain. (The default domain is determined by a parameter in the server's SQLNET.ORA file. See the section on the SQLNET.ORA file in Appendix A of this manual.)
Prior to Oracle7, a database administrator could specify any linkname for a database link. However, with Oracle7 and later, a database link must have the same name as the global database name of the database. Remember that the service name is also the same as the global database name; therefore, the linkname and service name are now the same.
For example, the command for creating a public database link to a database which has the global database name ORCHID.HQ.ACME is as follows:
CREATE PUBLIC DATABASE LINK ORCHID.HQ.ACME CONNECT TO scott IDENTIFIED BY tiger USING 'ORCHID.HQ.ACME'
Note: The CONNECT TO username IDENTIFIED BY password clause and the USING 'global_database_name' clause are both optional.
CREATE PUBLIC DATABASE LINK NY_FIN.HQ.ACME USING 'NY_FIN.HQ.ACME'

Figure 5 - 2. Public Database Link with Default Connection
Users connected to OHIO.SALES.ACME can use the NY_FIN.HQ.ACME database link to connect to NY_FIN.HQ.ACME with the same username and password they have on OHIO.SALES.ACME. To access the table on NY_FIN.HQ.ACME called EMP, any user could issue the SQL query:
SQL> SELECT * FROM EMP@NY_FIN.HQ.ACME;
Note: If the target database were in the default domain of the source database, the user would not need to include the domain in the link name or service name, or in the SELECT command.
This query would initiate a connection from OHIO to NY_FIN using the current username and password to log onto NY_FIN. The query would then be processed on NY_FIN, and the data available to the current user from the table EMP would be returned to OHIO. Each user creates a separate connection to the server. Subsequent queries to that database link by that user would not require an additional logon.
CREATE PUBLIC DATABASE LINK NY_FIN CONNECT TO FINPUBLIC IDENTIFIED BY NOPASS USING 'NY_FIN'
Note: The CONNECT TO username IDENTIFIED BY password clause and the USING 'global_database_name' clause are both optional.
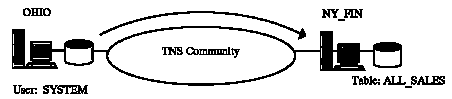
Figure 5 - 3. Public Database Link with Specific Connection
Any user connected to OHIO can use the NY_FIN database link to connect to NY_FIN with the common username/password of FINPUBLIC/NOPASS. To access the table in the FINPUBLIC account of NY_FIN called ALL_SALES, any user could issue the SQL query:
SQL> SELECT * FROM ALL_SALES@NY_FIN;
This query would initiate a connection from OHIO to NY_FIN to the common account FINPUBLIC. The query would be processed on NY_FIN and data from the table ALL_SALES would be returned to OHIO.
Each user creates a separate connection to the common account on the server. Subsequent queries to that database link by that user would not require an additional logon.
A connection qualifier contains a qualifier name and, optionally, a username and password. To create a connection qualifier, use a statement similar to the following:
CREATE PUBLIC DATABASE LINK NY_FIN@PROFITS CONNECT TO ACCOUNTS IDENTIFIED BY TAXES USING 'NY_FIN'
To use the connection qualifier, you append the qualifier name to the service name of the database you want to access.
For example, the following SQL queries use three separate database links to the same database, using different connection qualifiers:
SELECT * FROM EMP@NY_FIN;
SELECT * FROM SCHEDULE@NY_FIN@PROFITS;
SELECT * FROM EMPSALARIES@NY_FIN@FIN;
In this example @PROFITS and @FIN are connection qualifiers.
DROP DATABASE LINK linkname;
For example, to drop the database link NY_FIN, the command would be:
DROP DATABASE LINK NY_FIN;
SQL> SELECT * FROM EMP@OHIO, DEPT@NY_FIN;
For a more detailed discussion of database links, see Oracle7 Server Distributed Systems, Volume I, and the Oracle Names Administrator's Guide.
CREATE [PUBLIC] SYNONYM_name FOR [schema.]object_name[@database_link_name]
In this syntax:
[PUBLIC]
Specifies that this synonym is available to all users. Omitting this parameter makes a synonym private, and usable only by the creator. Public synonyms can be created only by a user with CREATE PUBLIC SYNONYM system privilege.
synonym_name
Specifies the alternate object name to be referenced by users and applications.
schema
Specifies the schema of the object specified in object_name. Omitting this parameter uses the creator's schema as the schema of the object.
object_name
Specifies either a table, view, sequence, or other name as appropriate.
database_link_name
Specifies the database link which identifies the remote username in which the object specified in object_name is located.
A synonym must be a uniquely named object for its schema. If a schema contains a database object and a public synonym exists with the same name, Oracle always finds the database object when the user that owns the schema references that name.
Figure 5 - 4 shows two servers, OHIO and NY_FIN, in which a database link from OHIO to NY_FIN and the synonym FOR_SALE provide an alternate object name for use in OHIO to reference the OPEN table in NY_FIN. The database link and the synonym are created as follows:
CREATE PUBLIC DATABASE LINK NY_FIN CONNECT TO REAL_ESTATE IDENTIFIED BY NOPASS; USING 'NY_FIN' CREATE PUBLIC SYNONYM FOR_SALE FOR OPEN@NY_FIN;

Figure 5 - 4. Using Synonyms for Alternate Object Names
The table OPEN on NY_FIN could be accessed from OHIO using the SQL statement:
SELECT * FROM FOR_SALE;
Using this database link, the user is logging on to NY_FIN as user REAL_ESTATE. Notice that this public synonym was created by the DBA on behalf of the REAL_ESTATE username. If the table OPEN were owned by another user, such as SALES_MGR, the CREATE SYNONYM statement would have referred to the object as SALES_MGR.OPEN@NY_FIN. Without such a prefix, a table that does not exist in the database link user's schema would return an error, since it would be looking for the OPEN table owned by the REAL_ESTATE user.
This ability to isolate applications from the location of data in a distributed transaction ensures maximum flexibility for future enhancements or changes to the application. For example, if the OPEN table were to move from one database server to another, only the synonym or the database link would need to be changed to identify the new location. The applications would continue to reference the same object name, although they would be connecting to a new location to access the data in that table. Figure 5 - 5 shows the most common method of redefining the location of a table to retain location transparency.
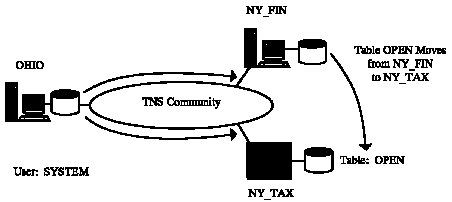
Figure 5 - 5. Redefining Table Location to Retain Location Transparency
CREATE PUBLIC DATABASE LINK NY_TAX CONNECT TO REALTOR IDENTIFIED BY NOPASS USING 'NY_TAX' DROP SYNONYM FOR_SALE;
CREATE PUBLIC SYNONYM FOR_SALE FOR OPEN@NY_TAX;
To relocate the table, a second database link was created called NY_TAX that connected to a new database with the service name NY_TAX, and the synonym was recreated to reference the NY_TAX database link instead of the NY_FIN database link. Any other tables that were accessed through the NY_FIN database link to NY_FIN would continue to function properly.
Alternatively, if the only table being accessed on NY_FIN were the OPEN table, the synonym could have remained unchanged and the database link redefined to use the service name NY_TAX instead of NY_FIN. Either option is equally effective.
Maintaining snapshots of a master table among the nodes of a distributed database is often a useful feature for the following reasons:
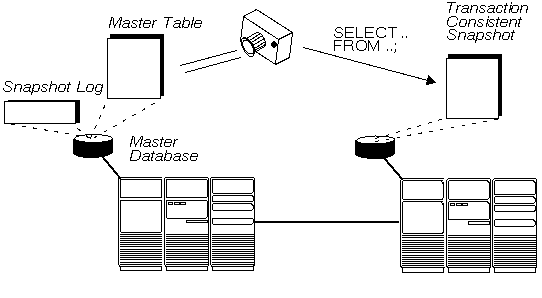
Figure 5 - 6. Table Replication Using Snapshots
A snapshot is a full copy or a subset of a table that reflects a recent state of the master table. A snapshot is defined by a distributed query that references one or more master tables, view, or other snapshots. A database that contains a master table is referred to as the master database.
Simple vs. Complex Snapshots Each row in a simple snapshot is based on a single row in a single remote table. Therefore, a simple snapshot's defining query has no GROUP BY or CONNECT BY clauses, or subqueries, joins, or set operations. If a snapshot's defining query contains any of these clauses or operations, it is referred to as a complex snapshot.
CREATE SNAPSHOT emp_sf
PCTFREE 5 PCTUSED 60
TABLESPACE users
STORAGE (INITIAL 50K NEXT 50K PCTINCREASE 50)
REFRESH FAST
START WITH sysdate
NEXT sysdate + 7
AS SELECT * FROM scott.emp@ny;Whenever a snapshot is created, it is immediately populated with the rows returned by the query that defines the snapshot. Thereafter, the snapshot is refreshed as specified by the REFRESH clause; see Oracle7 Server Distributed Systems, Volume 2: Replicated Data for more information about refreshing snapshots.
When a snapshot is created, Oracle creates several internal objects in the schema of the snapshot. These objects should not be altered. At the snapshot node, Oracle creates a base table to store the rows retrieved by the snapshot's defining query. Oracle then creates a read-only view of this table that is used whenever queries are issued against the snapshot.
Specifying the Defining Query of a Snapshot The defining query of a snapshot can be any valid query of tables, views, or other snapshots that are not owned by user SYS. The query cannot contain either an ORDER BY or FOR UPDATE clause. Furthermore, simple snapshots are defined using a query that does not contain GROUP BY or CONNECT BY clauses, or join, subquery, or set operations.
The query that defines a snapshot can define a snapshot with a different structure from that of the master table. For example, the following CREATE SNAPSHOT statement creates a local snapshot named EMP_DALLAS, with only the EMPNO, ENAME, and MGR columns of the master table (in New York), and only the rows of the employees in department 10:
CREATE SNAPSHOT emp_dallas
.
.
.
AS SELECT empno, ename, mgr
FROM scott.emp@ny
WHERE deptno = 10;Privileges Required to Create Snapshots To create a snapshot, the following sets of privileges must be granted as follows:
The large set of privileges required to create a snapshot is due to the underlying objects that must also be created on behalf of the snapshot.
A complex snapshot or simple snapshot without a snapshot log must be completely regenerated using the master tables every time the snapshot is refreshed (called a complete refresh).
CREATE SNAPSHOT LOG ON emp TABLESPACE users STORAGE (INITIAL 10K NEXT 10K PCTINCREASE 50);
The snapshot log is always created in the same schema that contains the master table. Since you cannot specify a name for the snapshot log (one is implicitly given by Oracle), uniqueness is not a concern.
If you own the master table, you can create an associated snapshot log if you have the CREATE TABLE and CREATE TRIGGER system privileges. If you are creating a snapshot log for a table in another user's schema, you must have the CREATE ANY TABLE and CREATE ANY TRIGGER system privileges. In either case, the owner of the snapshot log must have sufficient quota in the tablespace intended to hold the snapshot log.
The privileges required to create a snapshot log directly relate to the privileges necessary to create the underlying objects associated with a snapshot log.
SELECT * FROM emp;
To query a snapshot, you must have the SELECT object privilege for the snapshot, either explicitly or via a role.
In release 7.0 of the Oracle Server, snapshots are read-only. You cannot issue any INSERT, UPDATE, or DELETE statements when using a snapshot; if you do, an error is returned. Although INSERT, UPDATE, and DELETE statements can be issued against the base table for a snapshot, they can corrupt the snapshot. Never manipulate data in the base table of a snapshot. Updates are allowed on the master table only, which must then be refreshed to update the snapshot.
Creating Views and Synonyms Based on Snapshots Views or synonyms can be defined based on snapshots. The following statement creates a view based on the EMP snapshot:
CREATE VIEW sales_dept AS SELECT ename, empno FROM emp WHERE deptno = 10;
DROP SNAPSHOT emp;
If you drop the only snapshot of a master table, you should also drop the snapshot log of the master table, if appropriate.
Only the owner of a snapshot, or a user with the DROP ANY SNAPSHOT, DROP ANY TABLE, and DROP ANY VIEW system privileges can drop a snapshot.
For more information about table replication, snapshots, and distributed database design, refer to the following manuals: Oracle7 Server Distributed Systems, Volumes I and II, and the Oracle7 Server Administrator's Guide.
COPY FROM username/password@service_name [TO username/password@service_name] (APPEND | CREATE | INSERT | REPLACE) tablename [columnlist] USING subquery
In this syntax:
service_name
Specifies a valid service name in the TNSNAMES.ORA file. Each service name maps to a connect descriptor that connects to a database using the keyword SID.
APPEND
Specifies that if the destination table already exists, COPY will insert the copied data into it. If the table does not already exist, COPY will create it and then insert the copied data into it.
CREATE
Specifies that COPY will create a new table and insert the copied data into it. If the table already exists, COPY will report an error and stop processing.
INSERT
Specifies that if the destination table already exists, COPY will insert the data into it. If the table does not already exist, COPY will report an error and stop processing.
REPLACE
Specifies that if the table already exists, it will be dropped and replaced with the new data. If the table does not already exist, it will be created and the data inserted into it.
tablename
Specifies the destination table to which you are copying data.
columnlist
Specifies that only data from the specified columns should be copied.
subquery
Specifies the query to be used to select the data to be copied.
Note that you can use any kind of query to select the data to be copied. For example, you can COPY select rows from the source table by using a WHERE clause. You can also COPY specific columns from the source table by listing those columns after the SELECT statement, instead of using the asterisk that means all columns. The copied columns will have the same names in the destination table that they had in the source table.
Following is an example of a COPY command that copies only two columns from the source table specified by the alias BOSTON, and copies only those rows in which the value of DEPTNO is 30. Since the TO clause is omitted, the table is copied to the database to which SQL*Plus is currently connected:
COPY FROM SCOTT/TIGER@BOSTON REPLACE EMPCOPY2 USING SELECT ENAME, SAL FROM EMP WHERE DEPTNO = 30;
In the following example, the command copies the entire table EMP from the remote database specified by the SALES service name in the TNSNAMES.ORA file. Because the TO clause is omitted, the table is copied to the database to which SQL*Plus is currently connected. The new table is named EMP2:
COPY FROM SCOTT/TIGER@SALES CREATE EMP2 USING SELECT * FROM EMP;
You can also copy data to a local table from a remote table using the syntax:
COPY FROM SCOTT/TIGER@servicename INSERT INTO local_table SELECT * FROM remote_table@dblink
For further information about the COPY command, see the SQL*Plus User's Guide and Reference Manual.
Extending this notion over a network, operating system authorized logins allow users to log into a database on a remote machine using their local userid, without supplying a database password. The operating system user account must match the username of the operating system authorized account.
For further information about user authentication, see the Oracle7 Server Distributed Systems, Volume I.
If you have applications that rely on operating system authorized logins across a network, you should consider altering them to require the user to supply a password when connecting over the network.
In SQL*Net version 1 the ability to perform operating system authorized logins exists in some SQL*Net TCP/IP and SQL*Net DECnet drivers on UNIX and VMS systems. The default setting is for operating system authorized logins to be enabled unless explicitly disabled. We recommend that you explicitly disable operating system authorized logons where they exist in any version 1 drivers you have installed. For information regarding your platform and SQL*Net Version 1 drivers, and how operating system authorized logins can be disabled, see your Oracle operating system specific manuals regarding SQL*Net version 1.
In SQL*Net version 2, operating system authorized login support is enhanced to make it more difficult to act as an imposter, but it is still not impossible. By default, operating system authorized logins are disabled in SQL*Net version 2.
Note: If externally authenticated logins are enabled (by setting the REMOTE_OS_AUTHENT parameter to TRUE), it will be possible to connect without a password even though the underlying SQL*Net protocol cannot verify the identity of the user. For this reason, REMOTE_OS_AUTHENT should always be set to FALSE (the default value). If it is necessary to make externally authenticated logins, then a secure protocol such as the Bequeath (Pipe) driver should be used.
In all cases with SQL*Net version 1 or version 2, Oracle recommends leaving remote DBA privileges disabled.
A discussion of security issues in networked systems is in Chapter 6 of Oracle7 Server Distributed Systems, Volume I.
Network Identity
All authentication services provide the concept of a network identity so that no matter which machine a user is logged into, he or she can log onto the network and be identified as the same person. This method of authentication ensures that a user is who he or she claims to be.
Note: External authentication refers to authentication by either a network service or the operating system. OS authentication refers to operating system authorization only.
SVRMGR> CONNECT /@ny Connected.
If an authentication adapter is available, the server will use it to find the user's network identity. If an authentication adapter is not available, operating system authorization will be performed. If the connection is not secure, the value of REMOTE_OS_AUTHENT will be used to determine if the login may proceed.
Note: It is highly recommended that REMOTE_OS_AUTHENT be set to FALSE, because most protocols are not secure.
Configuring external roles varies depending on the authentication service. Instead of using the SID to name network roles (as OS roles does), network roles use the global database name. For example, for DCE authentication, something similar to the following naming convention to configure roles would be used:
ORA_<global_database_name>_<role_name>[_[A][D]]
Note: Exact syntax to define network roles and privileges may vary depending on the authentication adapter in use.
Remote authentication provides a network version of the OSDBA and OSOPER privileges: SYSDBA and SYSOPER refer to the privileges necessary to perform an internal connection, whether verified by the operating system, password file, or network. A format similar to the following would be used to define network privileges:
ORA_<global_database_name>_[DBA|OPER]_SYS
See the Oracle Advanced Networking Option Administrator's Guide for information on configuring network roles and privileges for specific authentication adapters.
|
Prev Next |
Copyright © 1996 Oracle Corporation. All Rights Reserved. |
Library |
Product |
Contents |
Index |