| Oracle® Database Java Developer's Guide 10g Release 1 (10.1) Part Number B12021-01 |
|
|
View PDF |
| Oracle® Database Java Developer's Guide 10g Release 1 (10.1) Part Number B12021-01 |
|
|
View PDF |
Security is a large arena that includes network security for the connection, access and execution control of operating system resources or of JVM-defined and user-defined classes, and bytecode verification of imported JAR files from an external source. The following sections describe the various security support available for Java applications within Oracle Database.
The two major aspects to network security are authentication and data confidentiality. The type of authentication and data confidentiality is dependent on how you connect to the database--through Oracle Net or JDBC connection.
| Connection Security | Description |
|---|---|
|
Oracle Net |
The database can require both authentication and authorization before allowing a user to connect to it. Oracle Net database connection security can require one or more of the following:
|
|
JDBC |
The JDBC connection security that is required is similar to the constraints required on an Oracle Net database connection. In addition to the books listed in the Oracle Net database connection section, see the Oracle Database JDBC Developer's Guide and Reference. |
Once you are connected to the database, you still must have the correct Java 2 Permissions and database privileges to access the resources stored within the database. These resources include the following:
These resources can be protected by the following two methods:
| Resource Security | Description |
|---|---|
|
Database Resource Security |
Authorization for database resources requires that database privileges (not the same as the Java 2 security permissions) are granted to resources. For example, database resources include tables, classes, and PL/SQL packages. For more information, see the Oracle Database Application Developer's Guide - Fundamentals. All user-defined classes are secured against users from other schemas. You can grant execution permission to other users/schemas through an option on the |
|
JVM Security |
OracleJVM uses Java 2 security, which uses Permission objects to protect operating system resources. Java 2 security is automatically installed upon startup and protects all operating system resources and OracleJVM classes from all users, except See "Java 2 Security" for how to manage and modify Java 2 Permissions and policies. |
Each user or schema must be assigned the proper permissions to access operating system resources. For example, this includes sockets, files, and system properties.
Java 2 security was created to provide a flexible, configurable security for Java applications. With Java 2 security, you can define exactly what permissions on each loaded object that a schema or role will have. In release 8.1.5, the security provided you the choice of two secure roles:
JAVAUSERPRIV--few Permissions, including examining propertiesJAVASYSPRIV--major Permissions, including updating OracleJVM protected packages
Because OracleJVM security is based on Java 2 security, you assign Permissions on a class by class basis. Permissions contains two string attributes:
These permissions are assigned through database management tools. Each permission is encapsulated in a Permission object and is stored within a Permission table. The methods for managing all permissions are the subject for most of this chapter.
Java security was created for the non-database world. When you apply the Java 2 security model within the database, certain differences manifest themselves. For example, Java 2 security defines that all applets are implicitly untrusted, and all classes within the CLASSPATH are trusted. In Oracle Database, all classes are loaded within a secure database; thus, no classes are trusted.
The following table briefly describes the differences between the Sun Microsystems Java 2 security and the Oracle Database security implementation. This table assumes that you already understand the Sun Microsystems Java 2 security model. For more information, we recommend the following books:
As with Java 2 security, Oracle Database supports the security classes. Normally, you set the Permissions for the code base either through a tool or by editing the security policy file. In Oracle Database, you set the Permissions dynamically through DBMS_JAVA procedures. These procedures modify a policy table, which is a new table within the database that exclusively manages Java 2 security Permissions.
Two views have been created for you to view the policy table: USER_JAVA_POLICY and DBA_JAVA_POLICY. Both views contain information about granted and limitation Permissions. The DBA_JAVA_POLICY view can see all rows within the policy table; the USER_JAVA_POLICY table can see only Permissions relevant to the current user. The following is a description of the rows within each view:
| Table Column | Description |
|---|---|
|
Kind |
GRANT or RESTRICT. Shows whether this Permission is a positive (GRANT) or a limitation (RESTRICT) Permission. |
|
Grantee |
The name of the user, schema, or role to which the Permission object is assigned. |
|
Permission_schema |
The schema in which the Permission object is loaded. |
|
Permission_type |
The Permission class type, which is designated by a string containing the full class name, such as, |
|
Permission_name |
The target attribute (name) of the Permission object. You use this name when defining the Permission. When defining the target for a Permission of type PolicyTablePermission, the name can become quite complicated. See "Acquiring Administrative Permission to Update Policy Table" for more information. |
|
Permission_action |
The action attribute for this Permission. Many Permissions expect a null value if no action is appropriate for the Permission. |
|
Status |
ACTIVE or INACTIVE. After creating a row for a Permission, you can disable or re-enable it. This column shows the status of whether the Permission is enabled (ACTIVE) or disabled (INACTIVE). |
|
Key |
Sequence number you use to identify this row. This number should be supplied when disabling, enabling, or deleting the Permission. |
There are two ways to set your Permissions:
To set individual Permissions within the policy table, you must provide the following information:
You can either grant Java 2 Permissions or create your own. The Java 2 Permissions are listed in Table 9-1. If you would like to create your own Permissions, see "Creating Permissions".
You can grant permissions using either SQL or Java, as shown below. However, each returns a row key identifier that identifies the row within the permission table. In the Java version of DBMS_JAVA, each method returns the row key identifier, either as a returned parameter or as an OUT variable in the parameter list. In the PL/SQL DBMS_JAVA package, the row key is returned only in the procedure that defines the key OUT parameter. This key is used to enable and disable specific Permissions. See "Enabling or Disabling Permissions" for more information.
If, after executing the grant, a row already exists for the exact Permission, no update occurs, but the key for that row is returned. If the row was disabled, executing the grant enables the existing row.
Granting Permissions using the DBMS_JAVA package:
procedure grant_permission( grantee varchar2, permission_type varchar2, permission_name varchar2, permission_action varchar2 ) procedure grant_permission( grantee varchar2, permission_type varchar2, permission_name varchar2, permission_action varchar2, key OUT number)
Granting Permissions using Java:
long oracle.aurora.rdbms.security.PolicyTableManager.grant( java.lang.String grantee, java.lang.String permission_type, java.lang.String permission_name, java.lang.String permission_action); void oracle.aurora.rdbms.security.PolicyTableManager.grant( java.lang.String grantee, java.lang.String permission_type, java.lang.String permission_name, java.lang.String permission_action, long[] key);
Limiting Permissions using the DBMS_JAVA package:
procedure restrict_permission( grantee varchar2, permission_type varchar2, permission_name varchar2, permission_action varchar2) procedure restrict_permission( grantee varchar2, permission_type varchar2, permission_name varchar2, permission_action varchar2, key OUT number)
Limiting Permissions using Java:
long oracle.aurora.rdbms.security.PolicyTableManager.restrict( java.lang.String grantee, java.lang.String permission_type, java.lang.String permission_name, java.lang.String permission_action);
void oracle.aurora.rdbms.security.PolicyTableManager.restrict( java.lang.String grantee, java.lang.String permission_type, java.lang.String permission_name, java.lang.String permission_action, long[] key);
Assuming that you have appropriate Permissions to modify the policy table, you use the grant_permission method within the DBMS_JAVA package to modify the PolicyTable to allow the user access to the indicated file. In this example, the user, Larry, has PolicyTable modification Permission. Within a SQL package, Larry grants permission to read and write a file to the user Dave.
connect larry/larry REM Grant DAVE permission to read and write the Test1 file. call dbms_java.grant_permission('DAVE', 'java.io.FilePermission', '/test/Test1', 'read,write'); REM commit the changes to the PolicyTable commit;
You use the restrict method for specifying a limitation or exception to general rules. A general rule is a rule where, in most cases, the Permission is true. However, there may be exceptions to this rule. For these exceptions, you specify a limitation Permission.
That is, if you have defined a general rule that no one can read or write for an entire directory, you can define a limitation on an aspect of this rule through the restrict method. For example, if you want to allow access to all files within the /tmp directory--except for your password file that exists in that directory--you would grant permission for read and write to all files within /tmp and limit read and write access to the password file.
If you want to specify an exception to the limitation, you would create an explicit grant Permission to override the limitation Permission. In the scenario mentioned above, if you want the file owner to still be able to modify the password file, you can grant a more explicit Permission to allow access to one user, which will override the limitation. OracleJVM security combines all rules to understand who really has access to the password file. This is demonstrated in the following diagram:
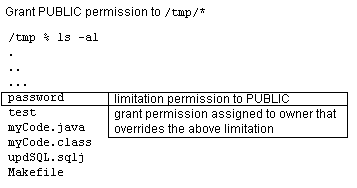
Text description of the illustration limitper.gif
The explicit rule is as follows:
If the limitation Permission implies the request, then for a grant to be effective, the limitation Permission must also imply the grant.
The following is the code that implements this example:
tmp.password file in /tmp.password file.
connect larry/larry REM Grant permission to all users (PUBLIC) to be able to read and write REM all files in /tmp. call dbms_java.grant_permission('PUBLIC', 'java.io.FilePermission', '/tmp/*', 'read,write'); REM Limit permission to all users (PUBLIC) from reading or writing the REM password file in /tmp. call dbms_java.restrict_permission('PUBLIC', 'java.io.FilePermission', '/tmp/password', 'read,write'); REM By providing a more specific rule that overrides the limitation, REM Larry can read and write /tmp/password. call dbms_java.grant_permission('LARRY', 'java.io.FilePermission', '/tmp/password', 'read,write'); commit;
All Permissions are rows within the policy table. As it is a table within the database and thus a resource, permission is needed to modify it. Specifically, the PolicyTablePermission object is required to modify the table. After the first initialization for OracleJVM, only a single role--JAVA_ADMIN--is granted the PolicyTablePermission to modify the policy table. The JAVA_ADMIN role is immediately assigned to DBA; thus, if you are assigned to the DBA group, you will automatically take on all JAVA_ADMIN Permissions.
For you to be able to add Permissions as rows to this table, JAVA_ADMIN must grant your schema update rights for the PolicyTablePermission. This Permission defines that your schema can add rows to the table. Each PolicyTablePermission is for a specific Permission type. For example, for you to add a Permission that controls access to a file, you must have a PolicyTablePermission that allows you to grant or limit a Permission on a FilePermission. Once this occurs, you have administrative Permission for FilePermission.
The administrator could grant and limit the PolicyTablePermissions in the same manner as other Permissions, but the syntax is complicated. For ease of use, use one of the following methods within the DBMS_JAVA package to grant administrative Permissions.
Granting policy table administrative Permissions using DBMS_JAVA:
procedure grant_policy_permission( grantee varchar2, permission_schema varchar2, permission_type varchar2, permission_name varchar2) procedure grant_policy_permission( grantee varchar2, permission_schema varchar2, permission_type varchar2, permission_name varchar2, key OUT number)
Granting policy table administrative permission using Java:
long oracle.aurora.rdbms.security.PolicyTableManager.grantPolicyPermission( java.lang.String grantee, java.lang.String permission_type, java.lang.String permission_name);
void oracle.aurora.rdbms.security.PolicyTableManager.grantPolicyPermission( java.lang.String grantee, java.lang.String permission_type, java.lang.String permission_name, long[] key);
The following example shows JAVA_ADMIN (as SYS) giving Larry permission to update the PolicyTable for FilePermission. Once this Permission is granted, Larry can grant permissions to other users for reading, writing, and deleting files.
REM Connect as SYS, which is assigned JAVA_ADMIN role, to give Larry permission REM to modify the PolicyTable connect SYS/SYS as SYSDBA REM SYS grants Larry the right to administer permissions for REM FilePermission call dbms_java.grant_policy_permission('LARRY', 'SYS', 'java.io.FilePermission', '*');
Create your own Permission type by performing the following steps:
1. Create and load the user Permission.
2. Grant administrative and action Permissions to specified users.
3. Implement security checks using the Permission.
Create your own Permission by extending the Java 2 Permission class. Any user-created Permission must extend Permission. The following example creates MyPermission, which extends BasicPermission, which in turn extends Permission.
package test.larry; import java.security.Permission; import java.security.BasicPermission; public class MyPermission extends BasicPermission { public MyPermission(String name) { super(name); } public boolean implies(Permission p) { boolean result = super.implies(p); return result; } }
When you create a Permission, you are designated as owner of that Permission. The owner is implicitly granted administrative Permission. This means that the owner can be an administrator for this Permission and can execute grant_policy_permission. Administrative Permission permits the user to update the policy table for the user-defined Permission.
For example, if LARRY creates a Permission, MyPermission, only LARRY can invoke grant_policy_permission for himself or another user. This method updates the PolicyTable on who can grant rights to MyPermission. The following code demonstrates this:
REM Since Larry is the user that owns MyPermission, Larry connects to REW the database to assign permissions for MyPermission. connect larry/larry REM As the owner of MyPermission, Larry grants himself the right to REM administer permissions for test.larry.MyPermission within the JVM REM security PolicyTable. Only the owner of the user-defined permission REM can grant administrative rights. call dbms_java.grant_policy_permission('LARRY', 'LARRY', 'test.larry.MyPermission', '*'); REM commit the changes to the PolicyTable commit;
Once you have granted administrative rights, you can grant action Permissions for the user-created Permission. For example, the following SQL grants permission for LARRY to execute anything within MyPermission and for DAVE to execute only actions that start with "act.".
REM Since Larry is the user that creates MyPermission, Larry connects to REW the database to assign permissions for MyPermission. connect larry/larry REM Once able to modify the PolicyTable for MyPermission, Larry grants himself REM full permission for MyPermission. Notice that the Permission is prepended REM with its owner schema. call dbms_java.grant_permission( 'LARRY', 'LARRY:test.larry.MyPermission', '*', null); REM Larry grants Dave permission to do any actions that start with 'act.*'. call dbms_java.grant_permission ('DAVE', 'LARRY:test.larry.MyPermission', 'act.*', null); REM commit the changes to the PolicyTable commit;
Once you have created, loaded, and assigned Permissions for MyPermission, you must implement the call to SecurityManager to have the Permission checked. There are four methods in the following example: sensitive, act, print, and hello. Because of the Permissions granted in the SQL example in step 2, the following users can execute methods within the example class:
act method.print and hello methods. The print method does not check any Permissions, so anyone can execute the print method. The hello method executes AccessController.doPrivileged, which means that the method executes with LARRY's Permissions. This is referred to as definer's rights.
package test.larry; import java.security.AccessController; import java.security.Permission; import java.security.PrivilegedAction; import java.sql.Connection; import java.sql.SQLException; /** * MyActions is a class with a variety of public methods that * have some security risks associated with them. We will rely * on the Java security mechanisms to ensure that they are * performed only by code that is authorized to do so. */ public class Larry { private static String secret = "Larry's secret"; MyPermission sensitivePermission = new MyPermission("sensitive"); /** * This is a security sensitive operation. That is it can * compromise our security if it is executed by a "bad guy". * Only larry has permission to execute sensitive. */ public void sensitive() { checkPermission(sensitivePermission); print(); } /** * Will print a message from Larry. We need to be * careful about who is allowed to do this * because messages from Larry may have extra impact. * Both larry and dave have permission to execute act. */ public void act(String message) { MyPermission p = new MyPermission("act." + message); checkPermission(p); System.out.println("Larry says: " + message); } /** * Print our secret key * No permission check is made; anyone can execute print. */ private void print() { System.out.println(secret); } /** * Print "Hello" * This method invokes doPrivileged, which makes the method run * under definer's rights. So, this method runs under Larry's * rights, so anyone can execute hello. Only Larry can execute hello */ public void hello() { AccessController.doPrivileged(new PrivilegedAction() { public Object run() { act("hello"); return null; } }); } /** * If a security manager is installed ask it to check permission * otherwise use the AccessController directly */ void checkPermission(Permission permission) { SecurityManager sm = System.getSecurityManager(); sm.checkPermission(permission); } }
Once you have created a row that defines a Permission, you can disable it so that it is no longer applied. However, if you decide you want the row action again, you can enable the row. You can delete the row from the table if you believe that it will never be used again. To delete, you must first disable the row. If you do not disable the row, the deletion will not occur.
To disable rows, you can use either the disable_permission or the revoke method.
revoke_permission method takes in parameters similar to the grant and restrict methods. It searches the entire policy table for all rows that match the supplied parameters.disable_permission method disables only a single row within the policy table. To do this, it takes in the policy table key. This key is also necessary to enable or delete a Permission. To retrieve the Permission key number, perform one of the following:
Disabling Permissions using DBMS_JAVA:
procedure revoke_permission(permission_schema varchar2, permission_type varchar2, permission_name varchar2, permission_action varchar2) procedure disable_permission(key number)
Disabling Permissions using Java:
void revoke(String schema, String type, String name, String action); void oracle.aurora.rdbms.security.PolicyTableManager.disable(long number);
Enabling Permissions using DBMS_JAVA:
procedure enable_permission(key number)
Enabling Permissions using Java:
void oracle.aurora.rdbms.security.PolicyTableManager.enable(long number);
Deleting Permissions using DBMS_JAVA:
procedure delete_permission(key number)
Deleting Permissions using Java:
void oracle.aurora.rdbms.security.PolicyTableManager.delete(long number);
Table 9-2 lists the installed Permission types. Whenever you want to grant or limit a Permission, you must provide the Permission type within the DBMS_JAVA method. The Permission types with which you control access are the following:
java.security.Permission
All the Java Permission types are documented in the Sun Microsystems Java 2 documentation.
The Oracle-specific Permissions, PolicyTablePermission and JServerPermission, are described below:
This Permission controls who can update the policy table. Once granted the right to update the policy table for a certain Permission type, the user can control other user's access to some resource.
After OracleJVM initialization, only the JAVA_ADMIN role can grant administrative rights for the policy table through PolicyTablePermission. Once it grants this right to other users, these users can in turn update the policy table with their own grant and limitation Permissions.
To grant policy table updates, use the DBMS_JAVA method:
grant_policy_permission, as discussed in "Acquiring Administrative Permission to Update Policy Table". Once you have updated the table, you can view either the DBA_JAVA_POLICY or USER_JAVA_POLICY views to see who has been granted Permissions.
Use this Permission to grant and limit access to OracleJVM resources. The JServerPermission extends from BasicPermission. The following table lists the names for which JServerPermission grants access:
When you first initialize OracleJVM, several roles are populated with certain Permission grants. The following tables show these roles and their initial Permissions:
JServerPermission, all users can load classes, except for the list of classes specified in the table. These exceptions are limitation Permissions. For more information on limitation Permissions, see Example 9-2.
| Permission Type | Permission Name | Action |
|---|---|---|
|
|
|
null |
|
|
* |
connect, resolve |
In release 8.1.5, Oracle8i JVM security was controlled by granting the roles of JAVASYSPRIV, JAVAUSERPRIV, or JAVADEBUGPRIV to schemas. In the current version, these roles still exist as Permission groups. See the previous section, "Initial Permission Grants" for the explicit Permissions set for each role. You can set up and define your own collection of Permissions. Once defined, you can grant any collection of Permissions to any user. That user will then have the same Permissions that exist within the role. In addition, if you need additional Permissions, you can add individual Permissions to either your specified user or role. Permissions defined within the policy table have a cumulative effect. See "Fine-Grain Definition for Each Permission" for information on how to grant Permissions to a user or a role.
The following example gives Larry and Dave the following Permissions:
REM Granting Larry the same permissions as exist within JAVASYSPRIV grant javasyspriv to larry; REM Granting Dave the ability to debug grant javadebugpriv to dave; commit; REM I also want Dave to be able to read and write all files on the system call dbms_java.grant_permission('DAVE', 'SYS:java.io.FilePermission', '<<ALL FILES>>', 'read,write', null);
A debug role, JAVADEBUGPRIV, was created to grant Permissions for running the debugger. The Permissions assigned to this role are listed in Table 9-7. To receive permission to invoke the debug agent, the caller must have been granted JAVADEBUGPRIV or the debug JServerPermission as follows:
REM Granting Dave the ability to debug grant javadebugpriv to dave; REM Larry grants himself permission to start the debug agent. call dbms_java.grant_permission ('LARRY', 'oracle.aurora.security.JServerPermission', 'Debug', null);
Although a debugger provides extensive access to both code and data on the server, its use should be limited to development environments. Refer to the discussion in "Debugging Server Applications" for information on using the debugging facilities in this release.
To load classes, you must have the following Permission:
JServerPermission("LoadClassInPackage." + <class_name>)
The class name is the fully qualified name of the class that you are loading.
This excludes loading into system packages or replacing any system classes. Even if you are granted permission to load a system class, Oracle Database prevents you from performing the load. System classes are classes that are installed by Oracle Database with CREATE JAVA SYSTEM. The following error is thrown if you try to replace a system class:
ORA-01031 "Insufficient privileges"
The following shows the ability of each user after database installation, including Permissions and OracleJVM restrictions:
java.*, oracle.aurora.*, oracle.jdbc.*. If the user wants to load such classes into another schema, it must be granted the JServerPermission(LoadClassInPackage.<class>) Permission.The following example shows how to grant SCOTT Permission to load classes into the oracle.aurora.* package:
dbms_java.grant_permission('SCOTT', 'SYS:oracle.aurora.tools.*', null);